Our researchers at Trojan Ninja have recently seen that the advanced persistent threat (APT) group Stately Taurus has exploited the widely-used Visual Studio Code software in espionage operations targeting government entities in Southeast Asia. Stately Taurus, a Chinese APT group known for its cyberespionage activities, utilized Visual Studio Code’s built-in reverse shell feature to establish a foothold in the target networks. This technique, identified by security researchers in 2023, is newly observed in the wild according to our telemetry and various other sources.
We believe this campaign is a direct extension of a previously reported operation, which we have believes that to Stately Taurus with moderate confidence. This assessment is based on the tactics, techniques, and procedures (TTPs), timeline, and the specific focus on government entities in Southeast Asia.
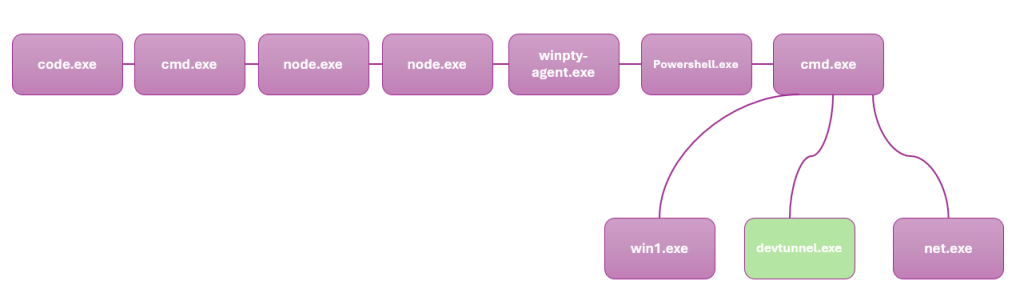
In September 2023, a campaign attributed to Stately Taurus that utilized the ToneShell backdoor as a primary tool. In this campaign, Stately Taurus employed ToneShell to compress files for exfiltration, securing the RAR archives with a distinct password. This password, consisting of 13 characters with a mix of upper and lower case letters and digits.
Additional TTPs Associated with the Stately Taurus Cluster
sshd.exe: The attacker utilized OpenSSH (sshd.exe) for command execution, file transfers, and lateral movement within the environment, OpenSSH enables users to remotely connect to machines via SSH.








